SharifCTF: SRM
This was the second reverse engineering challenge from SharifCTF. It was a little harder than the last one, but over all pretty easy. A few simple calculations and we get a flag.
The File Type
If we take a look at it we will see that it’s a GUI Windows PE32 program
$ file SRM.exe
SRM.exe: PE32 executable (GUI) Intel 80386, for MS WindowsTime to head to a Windows VM!
Analyzing the Execution
I opened it up in OllyDbg and broke on the call of the “OK” button. Doing this we can see that the first thing it does is take our input using an API and then checks our E-mail. If it finds the E-mail address as invalid, it quits.
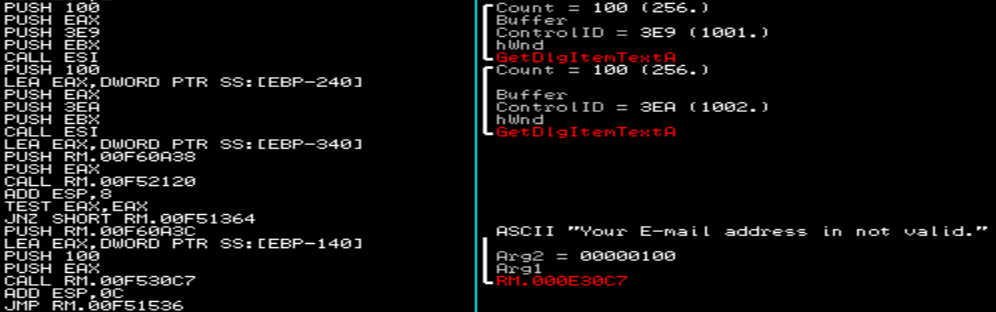
I usually like to jump in to all the calls of a program, even if I’m pretty sure I know what they do, to make sure that they don’t influence code later on. I ended up digging into that E-mail checking routine, and despite doing some cool functions with MMX instrucions, packing and unpacking a float to compare with '@Your E-Mail ', all it ends up doing is checking your email is in the form of *@*.com where * is a wildcard. It’s a bit of a misdirection, and if you spend too much time on that part this challenge takes more time than it’s worth.
With that in mind, we can enter any valid email and break later where it checks the serial.
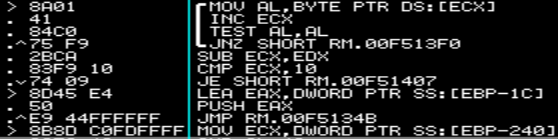
Here it loops through our input, byte-by-byte, and checks to ensure its length is 16 (0x10) characters. Now we know the length of our serial! Almost done. The next instructions, starting at the jump to 0x00F51407, do some hard-coded checks and calculations based on those to checks. I’ll go over one calculation, then construct psudo-code for the rest of the characters.
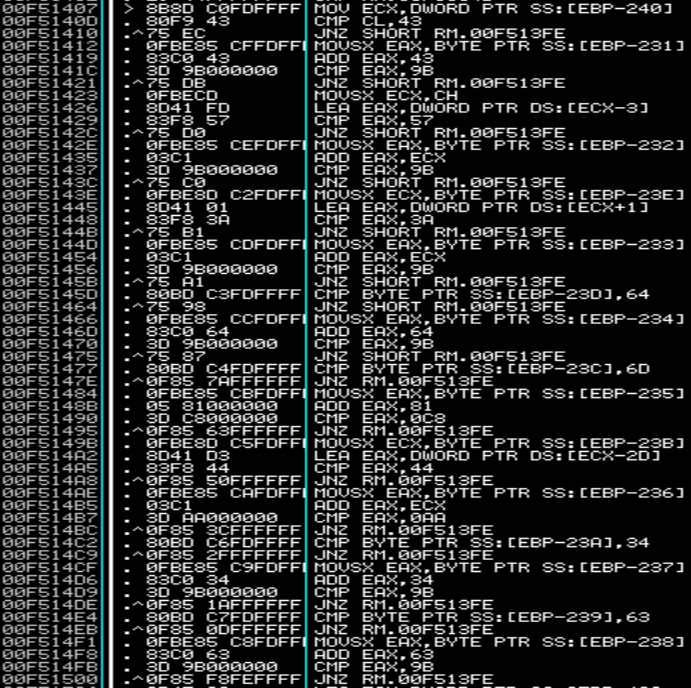
The first check is loading the first character of our input into ECX and then does a lower-byte compare to 0x43, or 'C'. After that it loads the last character of our given serial into EAX, adds 0x43 to it, and then compares that to 0x9B. This means our last character should be: 'X'
Checks of this nature are carried out, pairing the characters on each half of the serial and doing simple CMPs to test the results. Rather than go over each of these I wrote a model for the rest:
def testKey(key):
return( len(key) == 16 and (
key[0] == 'C'
and key[-1] == 'X'
and key[1] == 'Z'
and ord(key[1]) + ord(key[-2]) == 0x9b
and key[2] == '9'
and ord(key[2]) + ord(key[-3]) == 0x9b
and key[3] == 'd'
and key[-4] == '7'
and key[4] == 'm'
and key[-5] == 'G'
and key[5] == 'q'
and ord(key[5]) + ord(key[-6]) == 0xaa
and key[6] == '4'
and key[-7] == 'g'
and key[7] == 'c'
and key[-8] == '8'
))All that’s left to do now is solve this, which isn’t hard. Our key becomes: CZ9dmq4c8g9G7bAX. Testing that with our E-mail format does indeed produce the success message:
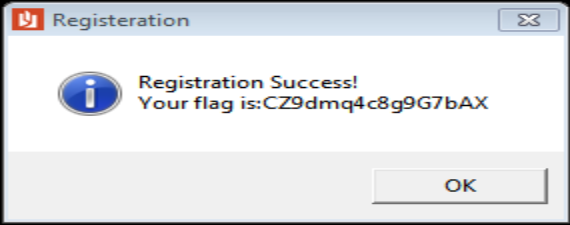
Final Flag: